How can I pass the Cisco CCNA 200-125 exam?You need the latest valid 200-125 dumps!Where to get it?Pass4itsure help you. https://www.pass4itsure.com/200-125.html trusted CCNA 200-125 dumps for the Cisco CCNA 200-125 exam.
What Should You Know(Cisco 200-125 Exam)
Last date to test: February 23, 2020
The 200-125 exam will be retired on February 23, 2020.
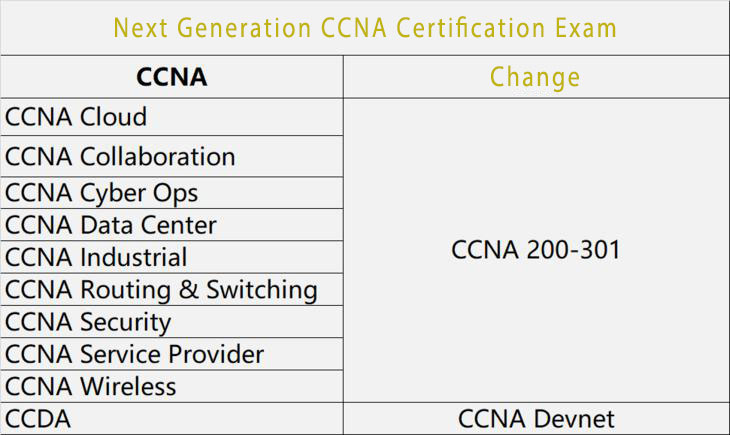
To achieve CCNA after February 24, you need to take the CCNA 200-301 exam.
About CCNA 200-301 exam https://www.cisco.com/c/dam/en_us/training-events/le31/le46/cln/marketing/exam-topics/200-301-CCNA.pdf
Trusted CCNA 200-301 exam dumps https://www.pass4itsure.com/200-301.htmlccna-2020jpgTrusted CCNA 200-301 exam dumps https://www.pass4itsure.com/200-301.html
Cisco Practice Tests:200-125 CCNA
QUESTION 1
Which command is needed to send RIPv2 updates as broadcast when configured for RIPv2?
A. ip rip v2-broadcast
B. ip rip receive version 1
C. ip rip receive version 2
D. version 2
Correct Answer: A
QUESTION 2
Which feature enables a router to pass DHCPOFFER messages to other interfaces on the same router?
A. DHCP server address exclusions
B. DNS helper addresses
C. DHCP smart-relay
D. DHCP server boot files
Correct Answer: C
QUESTION 3
What is the best way to verify that a host has a path to other hosts in different networks?
A. Ping the loopback address.
B. Ping the default gateway.
C. Ping the local interface address.
D. Ping the remote network.
Correct Answer: D
Ping is a tool that helps to verify IP-level connectivity; PathPing is a tool that detects packet loss over multiple-hop trips.
When troubleshooting, the ping command is used to send an ICMP Echo Request to a target host name or IP address.
Use Ping whenever you want to verify that a host computer can send IP packets to a destination host. You can also use
the Ping tool to isolate network hardware problems and incompatible configurations. If you call ipconfig /all and receive
a
response, there is no need to ping the loopback address and your own IP address — Ipconfig has already done so in
order to generate the report.
It is best to verify that a route exists between the local computer and a network host by first using ping and the IP
address of the network host to which you want to connect. The command syntax is:
ping
Perform the following steps when using Ping:
Ping the loopback address to verify that TCP/IP is installed and configured correctly on the local computer.
ping 127.0.0.1
If the loopback step fails, the IP stack is not responding. This might be because the TCP drivers are corrupted, the
network adapter might not be working, or another service is interfering with IP.
Ping the IP address of the local computer to verify that it was added to the network correctly. Note that if the routing
table is correct, this simply forwards the packet to the loopback address of 127.0.0.1.
ping
Ping the IP address of the default gateway to verify that the default gateway is functioning and that you can
communicate with a local host on the local network.
ping
Ping the IP address of a remote host to verify that you can communicate through a router.
ping
Ping the host name of a remote host to verify that you can resolve a remote host name.
ping
Run a PathPing analysis to a remote host to verify that the routers on the way to the destination are operating correctly.
pathping
QUESTION 4
which statement about recovering a password on a cisco router is true ?
A. it requires physical access to the router
B. the default reset password is cisco
C. a factory reset is required if you forget the password
D. it requires a secure SSL/VPN connection
Correct Answer: A
QUESTION 5
Where information about untrusted hosts are stored?
A. CAM table
B. Trunk table
C. MAC table
D. binding database
Correct Answer: D
QUESTION 6
Which two states are the port states when RSTP has converged? (Choose two.)
A. discarding
B. listening
C. learning
D. forwarding
E. disabled
Correct Answer: AD
There are only three port states left in RSTP that correspond to the three possible operational states. The 802.1D
disabled, blocking, and listening states are merged into a unique 802.1w discarding state.
STP (802.1D) Port State RSTP (802.1w) Port State Is Port Included in Active Topology? Is Port Learning MAC
Addresses? Disabled Discarding No No Blocking Discarding No No Listening Discarding Yes No Learning Learning Yes
Yes Forwarding Forwarding Yes Yes Reference:
http://www.cisco.com/en/US/tech/tk389/tk621/technologies_white_paper09186a0080094cf a.s html#states
QUESTION 7
Which three functions are major components of a network virtualization architecture? (Choose three.)
A. network access control
B. virtual network services
C. policy enforcement
D. authentication services
E. network resilience
F. path isolation
Correct Answer: ABF
Network virtualization architecture has three main components: + Network access control and segmentation of classes
of users: Users are authenticated and either allowed or denied into a logical partition. Users are segmented into
employees, contractors and consultants, and guests, with respective access to IT assets. This component identifies
users who are authorized to access the network and then places them into the appropriate logical partition. + Path
isolation:
Network isolation is preserved across the entire enterprise: from the edge to the campus to the WAN and back again.
This component maintains traffic partitioned over a routed infrastructure and transports traffic over and between
isolated
partitions. The function of mapping isolated paths to VLANs and to virtual services is also performed in component.+
Network Services virtualization:
This component provides access to shared or dedicated network services such as security, quality of service (QoS), and
address management (Dynamic Host Configuration Protocol [DHCP] and Domain Name System [DNS]). It also applies
policy per partition and isolates application environments, if required.
Reference:
http://www.cisco.com/c/en/us/products/collateral/switches/catalyst-6500-series-switches/white_paper_c11-531522.pdf
QUESTION 8
Which option describes a benefit of a point-to-point leased line?
A. full-mesh capability
B. flexibility of design
C. low cost
D. simplicity of configuration
Correct Answer: D
QUESTION 9
Which type of secure MAC address must be configured manually?
A. static
B. dynamic
C. sticky
D. bia
Correct Answer: A
QUESTION 10
Drag and drop the extended traceout option from the left onto the correct description on the right.
Select and Place:
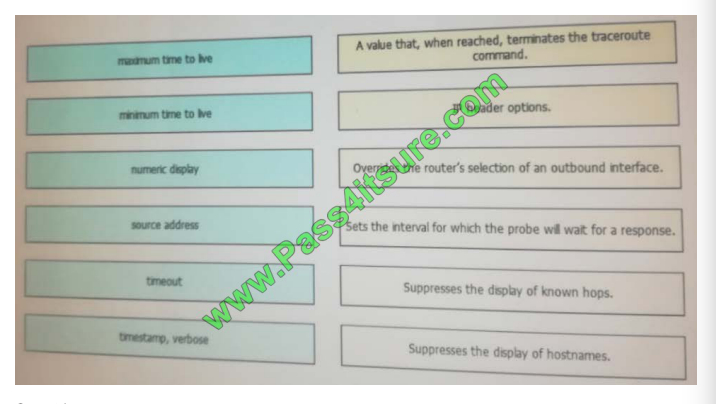
Correct Answer:

QUESTION 11
which configuration command can u apply to a HSRP router so that its local interface
becomes active if all other routers in the group fail?
A. no additional config is required
B. standby 1 track ethernet
C. standby 1 preempt
D. standby 1 priority 250
Correct Answer: A
QUESTION 12
What are two statement for SSH?
A. use port 22
B. unsecured
C. encrypted
D. most common remote-access method
E. operate at transport
Correct Answer: AC
QUESTION 13
Which three values can be included in the routing table of a router? (Choose three)
A. classful and classless destination addresses
B. source interfaces
C. Routgoing interfaces
D. source IP addresses
E. next hop IP address
F. destination IP addresses
Correct Answer: CDF

Pass4itsure 2020 PDF Dumps Free Download! – Google Drive
Pass4itsure 2020 Valid Cisco 200-125 PDF Dumps for Free Download!
https://drive.google.com/open?id=1YyJ8FHIihEE8EC0M05CgeYi8UbMUSC1I
Please access More Pass4itsure 200–125 questions/dumps (1316Q&As All, Updated Feb 15, 2020) here: https://www.pass4itsure.com/200-125.html.