
The latest 350-401 dumps contain 1061 latest exam questions and answers, and provide PDF and VCE learning methods, light and simple! The best CCNP Enterprise 350-401 ENCOR exam solution worth using.
The latest 350-401 dumps have been sorted out, audited, and actually verified by the CCNP Enterprise 350-401 ENCOR solution team. They are true and effective. They meet the candidate certification exam requirements and are guaranteed to pass the exam 100%!
Using the latest 350-401 exam questions and answers with PDF and VCE, please download the Latest 350-401 dumps: https://www.leads4pass.com/350-401.html.
Share some CCNP Enterprise 350-401 dumps exam questions for free
| From | Number of exam questions | Type | Online download | Associated certifications |
| Pass4itsure | 13 | Exam questions and answers | 350-401 PDF | CCNP Enterprise, Cisco |
QUESTION 1:
Which two statements about IP SLA are true? (Choose two)
A. It uses NetFlow for passive traffic monitoring
B. It can measure MOS
C. The IP SLA responder is a component in the source Cisco device
D. It is Layer 2 transport-independent correct
E. It uses active traffic monitoring correct
F. SNMP access is not supported
Correct Answer: DE
IP SLAs allow Cisco customers to analyze IP service levels for IP applications and services, increase productivity,
lower operational costs, and reduce the frequency of network outages.
IP SLAs use active traffic monitoring generation of traffic in a continuous, reliable, and predictable manner or measure network performance. Being Layer-2 transport independent, IP SLAs can be configured end-to-end over disparate networks to best reflect the metrics that an end-user is likely to experience.
QUESTION 2:
What is a characteristic of a traditional WAN?
A. low complexity and high overall solution scale
B. centralized reachability, security, and application policies
C. operates over DTLS and TLS authenticated and secured tunnels
D. united data plane and control plane
Correct Answer: D
QUESTION 3:
Which command set configures RSPAN to capture outgoing traffic from VLAN3 on interface GigabitEthernet 0/3 while
ignoring other VLAN traffic on the same interface?
A. monitor session 2 source interface gigabit ethernet 0/3 tx monitor session 2 filter vlan 1 – 2, 4 – 4094
B. monitor session 2 source interface gigabit ethernet 0/3 tx monitor session 2 filter vlan 3
C. monitor session 2 source interface gigabit ethernet 0/3 rx monitor session 2 filter vlan 1 – 2, 4 – 4094
D. monitor session 2 source interface gigabit ethernet 0/3 rx monitor session 2 filter vlan 3
Correct Answer: B
QUESTION 4:
A network engineer is configuring Flexible Netflow and enters these commands:
- Sampler Netflow1
- Mode random one out of 100
- Interface FastEthernet 1/0
- Flow-sampler netflow1
Which are two results of implementing this feature instead of traditional Netflow? (Choose two.)
A. CPU and memory utilization are reduced.
B. Only the flows of the top 100 talkers are exported
C. The data export flow is more secure.
D. The number of packets to be analyzed is reduced
E. The accuracy of the data to be analyzed is improved
Correct Answer: AD
Flow sampling reduces the CPU overhead of analyzing traffic with Flexible NetFlow by reducing the number of packets that are analyzed. Flow samplers are used to reduce the load on the device that is running by limiting the number of packets that are selected for analysis.
QUESTION 5:
Refer to the exhibit. A network engineer must log in to the router via the console, but the RADIUS servers are not
reachable. Which credentials allow console access?

A. the username “cisco” and the password “cisco123”
B. no username and only the password “test123”
C. no username and only the password “cisco123”
D. the username “cisco” and the password “cisco”
Correct Answer: C
We tested with GNS3 and the router only requires the password “cisco123” configured under the line console to authenticate. So we can deduce the “password” command under the line interface is preferred over the “login authentication” command.
QUESTION 6:
Which three methods does Cisco DNA Center use to discover devices? (Choose three.)
A. CDP
B. SNMP
C. LLDP
D. Ping
E. NETCONF
F. specified range of IP addresses
Correct Answer: ACF
There are three ways for you to discover devices:
1. Use Cisco Discovery Protocol (CDP) and provide a seed IP address.
2. Specify a range of IP addresses. (A maximum range of 4096 devices is supported.)
3. Use Link Layer Discovery Protocol (LLDP) and provide a seed IP address.
QUESTION 7:
Refer to the exhibit.
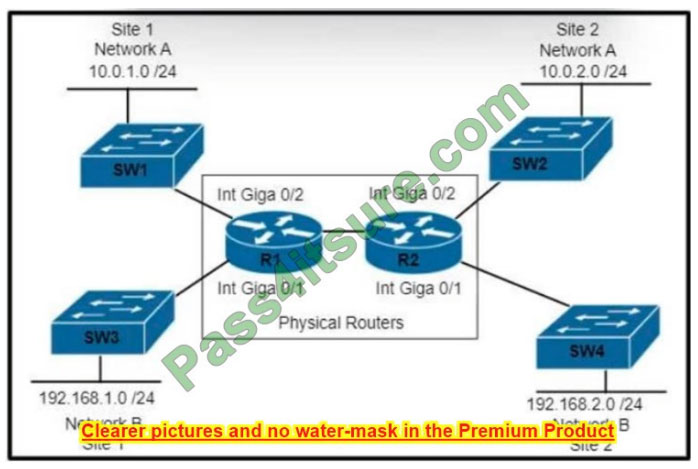
Which set of commands is required to configure and verify the VRF for Site 1 Network A on router R1?
A. R1#ip routing R1#(config)#ip vrf 100 R1#(config-vrf)#rd 100:1 R1#(config-vrf)# address family ipv4 !
R1(config)#interface Gi0/2 R1(config-if)#ip address 10.0.1.1 255.255.255.0 R1#show ip route
B. R1#ip routing R1#(config)#ip vrf 100 ! R1(config)#interface Gi0/2 R1(config-if)#ip address 10.0.1.1 255.255.255.0
R1#showip route
C. R1#ip routing R1#(config)#ip vrf 100 ! R1(config)#interface Gi0/2 R1(config-if)#ip vrf forwarding 100 R1(config-if)#ip
address 10.0.1.1 255.255.255.0 R1#show ip vrf
D. R1#ip routing R1#(config)#ip vrf 100 ! R1(config)#interface Gi0/2 R1(config-if)#ip address 10.0.1.1 255.255.255.0
R1#showip route
Correct Answer: C
QUESTION 8:
Refer to the exhibit.
A network engineer must simplify the IPsec configuration by enabling IPsec over GRE using IPsec profiles. Which two
configuration changes accomplish this? (Choose two).
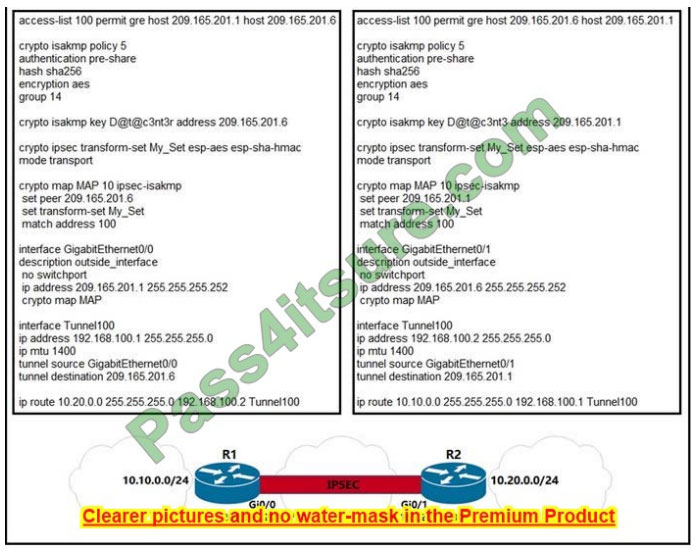
A. Create an IPsec profile, associate the transform-set ACL, and apply the profile to the tunnel interface.
B. Apply the crypto map to the tunnel interface and change the tunnel mode to tunnel mode ipsec ipv4.
C. Remove all configurations related to the crypto map from R1 and R2 and eliminate the ACL.
D. Create an IPsec profile, associate the transform set, and apply the profile to the tunnel interface.
E. Remove the crypto map and modify the ACL to allow traffic between 10.10.0.0/24 to 10.20.0.0/24.
Correct Answer: CD
A is wrong, you don’t use a “transform-set ACL”
B is wrong. the question states to use IPsec profiles. Crypto maps were the old way of doing ipsec tunnels before profiles.
C is correct, need to remove the crypto map config or it will cause some confusion if the tunnel profile is applied. Didn\’t lab it up, but the book references this.
D is correct, all you need to do is create a profile and associate the transform set to this profile, then apply it to the
tunnel. If no transform set was created you would have to create one.
E is wrong, I believe removing the crypto map would cause the traffic to flow unencrypted over the tunnel. acl in this case is to match the interesting traffic to be encrypted. it\’s denying it.
QUESTION 9:
A network administrator has designed a network with two multilayer switches on the distribution layer, which act as
default gateways for the end hosts. Which two technologies allow every end host in a VLAN to use both gateways?
(Choose two)
A. GLBP
B. HSRP
C. MHSRP
D. VSS
E. VRRP
Correct Answer: AD
VSS combines two switches into one logical switch.
both of them have their own control and data plane, and both of their data plane will keep alive, once the master control plane is down, the other take charge.
MHSRP sharp can\’t let all hosts use both gateways, 50% of host use gateway1, and another 50% of hosts use gateway 2 (from Windsor)
QUESTION 10:
When using BFD in a network design, which consideration must be made?
A. BFD is used with first-hop routing protocols to provide subsecond convergence.
B. BFD is more CPU-intensive than using reduced hold timers with routing protocols.
C. BFD is used with dynamic routing protocols to provide subsecond convergence.
D. BFD is used with NSF and graceful to provide subsecond convergence.
Correct Answer: C
https://www.cisco.com/en/US/docs/ios/12_4t/ip_route/configuration/guide/t_bfd.html
QUESTION 11:
DRAG DROP
Drag and drop the definitions on the left to their respective technological names on the right.
Select and Place:
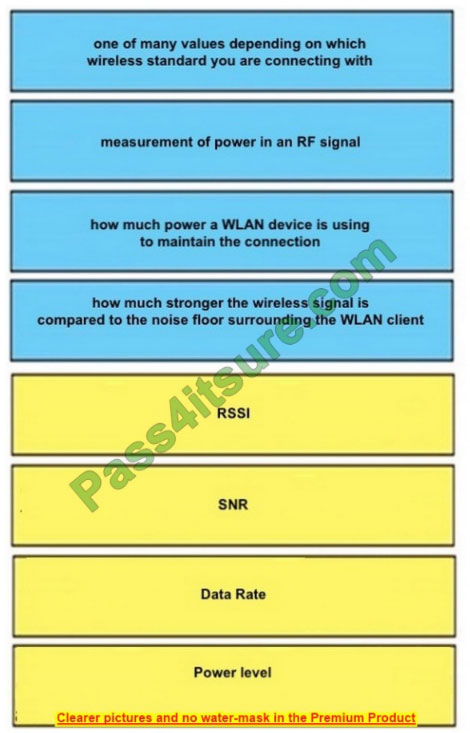
Correct Answer:

QUESTION 12:
Which data is properly formatted with JSON?

A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: B
B is correct, checked in JSONLint validator numbers 18 and 25 can be in ” or not still valid.
QUESTION 13:
Which method is used by an AP to join HA controllers and is configured in NVRAM?
A. stored WLC information
B. DNS
C. IP Helper Addresses
D. Primary/Secondary/Tertiary/Backup
Correct Answer: A
…
CCNP Enterprise 350-401 ENCOR certification: Test your knowledge and skills related to implementing core enterprise network technologies (Dual stack (IPv4 and IPv6) architecture, Virtualization, Infrastructure, Network assurance, Security, Automation) important certification!
Take this practice session to learn about the latest 350-401 exam questions and answers to help you improve your professional skills! Help you learn more about the latest CCNP Enterprise 350-401 ENCOR certification exam!
Now download CCNP Enterprise 350-401 ENCOR Best Exam solution: Latest 350-401 dumps https://www.leads4pass.com/350-401.html (1061 Q&A), use PDF or VCE to help you learn easily,
Successfully pass the CCNP Enterprise 350-401 ENCOR certification exam.