Pass4itsure 210-260 Dumps Exam Practice PDF, Most Popular Cisco 210-260 Dumps PDF Are The Best Materials, We Help You Pass Implementing Cisco Network Security. – pass4itsure 210-260 dumps pdf 329Q Full Version.
Pass4itsure Success:
Success
“I passed my exam earlier this morning. You know what I just use study materials from this site, no other books at all! It is really helpful if you do not get much time to prepare your exam. You should have a try. It won’t let you down. Why do you want to take roundabout ways if there is a shortcut.Trust me or not. Good luck to you all. Bob”
Awesome
“This is my first time to sit a Cisco exam, so you will know how nervous I was! Thanks for your help, Kingexam! I passed. I think 95% questions are more or less the same as your guidance. Some questions with the answer are in the different sequence, and, sorry to point out that one answer of your questions is incorrect, I’ll email you to let you know, you guys need to revise it. Well, I think your kingexam’s guidance is still more accurate than others. The most important thing is I got passed 🙂 Paul Hussler”
[Ensure Pass4itsure 210-451 PDF Dumps Exam From Google Drive]:https://drive.google.com/open?id=0BwxjZr-ZDwwWeFJLMDBQaDMyM1E
[Ensure Pass4itsure 210-260 PDF Dumps Exam From Google Drive]:https://drive.google.com/open?id=0BwxjZr-ZDwwWU0xad3NvRWR4Qzg
Cisco 210-260 Dumps Recommended Traing
The following course is the recommended training for this exam:
- Implementing Cisco Network Security (IINS) v3.0 – Self paced E-learning
- Implementing Cisco Network Security (IINS) v3.0 – Instructor-led training
Courses listed are offered by Cisco Learning Partners-the only authorized source for Cisco IT training delivered exclusively by Certified Cisco Instructors. Check the List of Learning Partners for a Cisco Learning Partner nearest you.
Latest and Most Accurate Pass4itsure 210-260 Dumps Exam Q&As(1-20)
QUESTION 1
Which three ESP fields can be encrypted during transmission? (Choose three.)
A. Security Parameter Index
B. Sequence Number
C. MAC Address
D. Padding
E. Pad Length
F. Next Header
210-260 exam Correct Answer: DEF
Explanation
QUESTION 2
What mechanism does asymmetric cryptography use to secure data?
A. a public/private key pair
B. shared secret keys
C. an RSA nonce
D. an MD5 hash
Correct Answer: A
Explanation
QUESTION 3
Whit which type of Leyer 2 attack can you “do something” for one host:
A. MAC spoofing
B. CAM overflow….
210-260 dumps Correct Answer: A
Explanation
QUESTION 4
Refer to the exhibit.
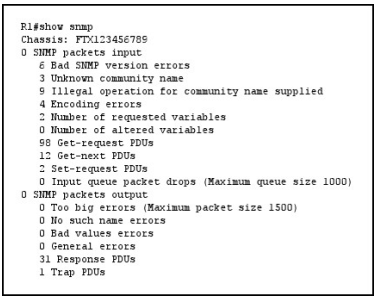
How many times was a read-only string used to attempt a write operation?
A. 9
B. 6
C. 4
D. 3
E. 2
Correct Answer: A
Explanation
QUESTION 5
Which feature allows a dynamic PAT pool to select the next address in the PAT pool instead of the next port of an existing address?
A. next IP
B. round robin
C. dynamic rotation
D. NAT address rotation
210-260 pdf Correct Answer: B
Explanation
QUESTION 6
Which label is given to a person who uses existing computer scripts to hack into computers lacking the expertise to write their own?
A. white hat hacker
B. hacktivist
C. phreaker
D. script kiddy
Correct Answer: D
Explanation
QUESTION 7
When Cisco IOS zone-based policy firewall is configured, which three actions can be applied to a traffic class? (Choose three.)
A. pass
B. police
C. inspect
D. drop
E. queue
F. shape
210-260 vce Correct Answer: ACD
Explanation
Explanation/Reference:
Zone-Based Policy Firewall Actions
ZFW provides three actions for traffic that traverses from one zone to another:
Drop — This is the default action for all traffic, as applied by the “class class-default” that terminates every inspect-type policy-map. Other class-maps within a policy-map can also be configured to drop unwanted traffic. Traffic that is handled by the drop action is “silently” dropped (i.e., no notification of the drop is sent to the relevant end-host) by the ZFW, as opposed to an ACL’s behavior of sending an ICMP “host unreachable” message to the host that sent the denied traffic. Currently, there is not an option to change the “silent drop” behavior. The log option can be added with drop for syslog notification that traffic was dropped by the firewall. Pass — This action allows the router to forward traffic from one zone to another. The pass action does not track the state of connections or sessions within the traffic. Pass only allows the traffic in one direction. A corresponding policy must be applied to allow return traffic to pass in the opposite direction. The pass action is useful for protocols such as IPSec ESP, IPSec AH, ISAKMP, and other inherently secure protocols with predictable behavior. However, most application traffic is better handled in the ZFW with the inspect action. Inspect–The inspect action offers state-based traffic control. For example, if traffic from the private zone to the Internet zone in the earlier example network is inspected, the router maintains connection or session information for TCP and User Datagram Protocol (UDP) traffic. Therefore, the router permits return traffic sent from Internet-zone hosts in reply to private zone connection requests. Also, inspect can provide application inspection and control for certain service protocols that might carry vulnerable or sensitive application traffic. Audit-trail can be applied with a parameter-map to record connection/session start, stop, duration, the data volume transferred, and source and destination addresses.
QUESTION 8
Which type of security control is defense in depth?
A. Threat mitigation
B. Risk analysis
C. Botnet mitigation
D. Overt and covert channels
Correct Answer: A
Explanation
QUESTION 9
Which statement about a PVLAN isolated port configured on a switch is true?
A. The isolated port can communicate only with the promiscuous port.
B. The isolated port can communicate with other isolated ports and the promiscuous port.
C. The isolated port can communicate only with community ports.
D. The isolated port can communicate only with other isolated ports.
210-260 exam Correct Answer: A
Explanation
QUESTION 10
Which statement about Cisco ACS authentication and authorization is true?
A. ACS servers can be clustered to provide scalability.
B. ACS can query multiple Active Directory domains.
C. ACS uses TACACS to proxy other authentication servers.
D. ACS can use only one authorization profile to allow or deny requests.
Correct Answer: A
Explanation
QUESTION 11
Refer to the exhibit.
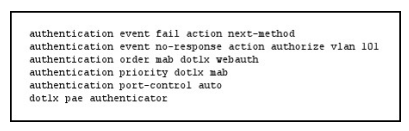
If a supplicant supplies incorrect credentials for all authentication methods configured on the switch, how will the switch respond?
A. The supplicant will fail to advance beyond the webauth method.
B. The switch will cycle through the configured authentication methods indefinitely.
C. The authentication attempt will time out and the switch will place the port into the unauthorized state.
D. The authentication attempt will time out and the switch will place the port into VLAN 101.
210-260 dumps Correct Answer: A
Explanation
QUESTION 12
What configure mode you used for the command ip ospf authentication-key c1$c0?
A. global
B. privileged
C. in-line
D. Interface
Correct Answer: D
Explanation
Explanation/Reference:
Explanation: ip ospf authentication-key is used under interface configuration mode, so it’s in interface level, under global configuration mode. If it asks about interface level then choose that. interface Serial0 ip address 192.16.64.1 255.255.25
QUESTION 13
Which two features are commonly used CoPP and CPPr to protect the control plane? (Choose two.)
A. QoS
B. traffic classification
C. access lists
D. policy maps
E. class maps
F. Cisco Express Forwarding
210-260 pdf Correct Answer: AB
Explanation
QUESTION 14
What is one requirement for locking a wired or wireless device from ISE?
A. The ISE agent must be installed on the device.
B. The device must be connected to the network when the lock command is executed.
C. The user must approve the locking action.
D. The organization must implement an acceptable use policy allowing device locking.
Correct Answer: A
Explanation
QUESTION 15
Which three statements are characteristics of DHCP Spoofing? (choose three)
A. Arp Poisoning
B. Modify Traffic in transit
C. Used to perform man-in-the-middle attack
D. Physically modify the network gateway
E. Protect the identity of the attacker by masking the DHCP address
F. can access most network devices
210-260 vce Correct Answer: ABC
Explanation
QUESTION 16
Which statement correctly describes the function of a private VLAN?
A. A private VLAN partitions the Layer 2 broadcast domain of a VLAN into subdomains
B. A private VLAN partitions the Layer 3 broadcast domain of a VLAN into subdomains
C. A private VLAN enables the creation of multiple VLANs using one broadcast domain
D. A private VLAN combines the Layer 2 broadcast domains of many VLANs into one major broadcast domain
Correct Answer: A
Explanation
QUESTION 17
which feature allow from dynamic NAT pool to choose next IP address and not a port on a used IP address?
A. next IP
B. round robin
C. Dynamic rotation
D. Dynamic PAT rotation
210-260 exam Correct Answer: B
Explanation
QUESTION 18
Which type of encryption technology has the broadcast platform support?
A. Middleware
B. Hardware
C. Software
D. File-level
Correct Answer: C
Explanation
QUESTION 19
When an IPS detects an attack, which action can the IPS take to prevent the attack from spreading?
A. Deny the connection inline.
B. Perform a Layer 6 reset.
C. Deploy an antimalware system.
D. Enable bypass mode.
210-260 dumps Correct Answer: A
Explanation
QUESTION 20
Which four tasks are required when you configure Cisco IOS IPS using the Cisco Configuration Professional IPS wizard? (Choose four.)
A. Select the interface(s) to apply the IPS rule.
B. Select the traffic flow direction that should be applied by the IPS rule.
C. Add or remove IPS alerts actions based on the risk rating.
D. Specify the signature file and the Cisco public key.
E. Select the IPS bypass mode (fail-open or fail-close).
F. Specify the configuration location and select the category of signatures to be applied to the selected interface(s).
Correct Answer: ABDF
Explanation
Explanation/Reference:
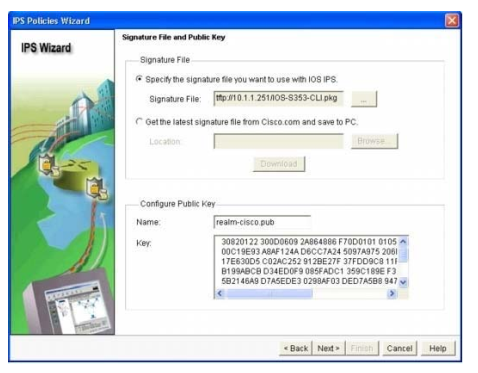
Step 11. At the `Select Interfaces’ screen, select the interface and the direction that IOS IPS will be applied to, then click `Next’ to continue
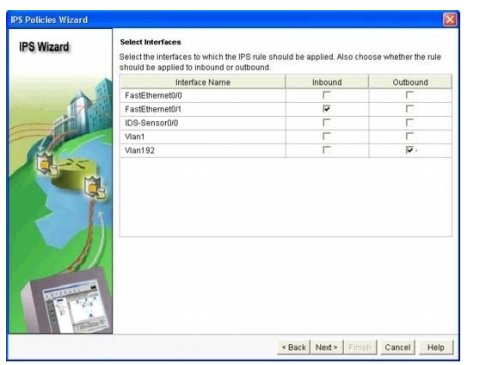
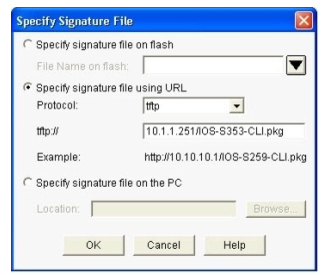
Step 12. At the `IPS Policies Wizard’ screen, in the `Signature File’ section, select the first radio button “Specify the signature file you want to use with IOS IPS”, then click the “…” button to bring up a dialog box to specify the location of the
signature package file, which will be the directory specified in Step 6. In this example, we use tftp to download the signature package to the router.
Step 13. In the `Configure Public Key’ section, enter `realm-cisco.pub’ in the `Name’ text field, then copy and paste the following public key’s key-string in the `Key’ text field. This public key can be downloaded from
Cisco.com at: http://www.cisco.com/pcgi-bin/tablebuild.pl/ios-v5sigup. Click `Next’ to continue.
30820122 300D0609 2A864886 F70D0101 01050003 82010F00 3082010A 02820101 00C19E93 A8AF124A D6CC7A24 5097A975 206BE3A2 06FBA13F 6F12CB5B 4E441F16 17E630D5 C02AC252 912BE27F 37FDD9C8 11FC7AF7
DCDD81D9 43CDABC3 6007D128
B199ABCB D34ED0F9 085FADC1 359C189E F30AF10A C0EFB624 7E0764BF 3E53053E
5B2146A9 D7A5EDE3 0298AF03 DED7A5B8 9479039D 20F30663 9AC64B93 C0112A35 FE3F0C87 89BCB7BB 994AE74C FA9E481D F65875D6 85EAF974 6D9CC8E3 F0B08B85
50437722 FFBE85B9 5E4189FF CC189CB9 69C46F9C A84DFBA5 7A0AF99E AD768C36
006CF498 079F88F8 A3B3FB1F 9FB7B3CB 5539E1D1 9693CCBB 551F78D2 892356AE 2F56D826 8918EF3C 80CA4F4D 87BFCA3B BFF668E9 689782A5 CF31CB6E B4B094D3
F3020301 0001
The Implementing Cisco Network Security (IINS) exam (210-260) is a 90-minute assessment with 60-70 questions. This exam tests a candidate’s ability to develop network applications in the Cisco environment. With the complete collection of questions and answers, Pass4itsure has assembled to take you through 329 Q&As to your 210-260 dumps exam preparation.
Exam Code: 210-260
Exam Name: Implementing Cisco Network Security
Q&As: 329
The Implementing Cisco Network Security (IINS) (210-260) exam is a 90-minute, 60-70 item exam that assesses how sales teams can effectively position in the CCNA Security. Some of the topics assessed are how to consider the challenges faced by business and IT today and how this relates to Cisco opportunities. The pass4itsure 210-260 dumps exam also assesses who “the customer” is and the importance of applications to many of the customers that are influential in purchasing application-based solutions. This certificate proves that the candidate has an advanced understanding within the Implementing Cisco Network Security.
Candidates who participate in the Cisco certification 210-260 dumps training materials should select exam practice questions and answers of pass4itsure, because pass4itsure is the best choice for you. With pass4itsure.com, you will have access to appropriate and best training materials so that you can directly start your real practice for the Cisco 210-260 exam.The recommended course have been carefully examined in order to create the Cisco 210-260 dumps tests.
Cisco 210-260 dumps exams cram will be your best choice for your real exam. We pass4itsure not only offer you the best dump exams but also golden excellent customer service. Pass4itsure.com covers all the pertinent areas and necessary guidelines to enable you to clear the Implementing Cisco Network Security 210-260 exam with minimum hassle. If you have some questions, welcome to have conversations with our online service persons. Or you could send Cisco 210-260 dumps test questions to our after-sale email, to contact us via email.
Pass4itsure Most Popular Cisco 210-260 Dumps Implementing Cisco Network Security Exam Practice PDF Are The Best Materials.