
This is a set of CCNA 200-301 practice exam materials provided by Pass4itsure, containing a total of 1,615 of the latest exam questions and answers, along with answer explanations.
VCE also offers a realistic scenario environment and analysis, as well as various question types. You can view the list of question types below:
| Total Q&As | 1615 |
| Single & Multiple Choice | 1394 |
| Drag Drop | 182 |
| Simulation Labs | 39 |
The CCNA exam features a diverse range of question types, and I am now sharing these latest practice exams online for free.
CCNA 200-301 Practice Exam
Freely provide the latest CCNA 200-301 exam questions and answers, and practice exams online.
| Launch time | Free Download |
| June 2025 | CCNA 200-301 PDF |
1.What is the purpose of a southbound API in a control based networking architecture?
A. Facilities communication between the controller and the applications
B. Facilities communication between the controller and the networking hardware
C. allows application developers to interact with the network
D. integrates a controller with other automation and orchestration tools.
Correct Answer: B
The Southbound Interface
In a controller-based network architecture, the controller needs to communicate to the networking devices. In most network drawings and architecture drawings, those network devices typically sit below the controller, as shown in Figure 16-5.
There is an interface between the controller and those devices, and given its location at the bottom part of drawings, the interface came to be known as the southbound interface, or SBI, as labeled in Figure 16-5.

2.DRAG DROP
Drag and drop the descriptions of AAA services from the left onto the corresponding services on the right.
Select and Place:
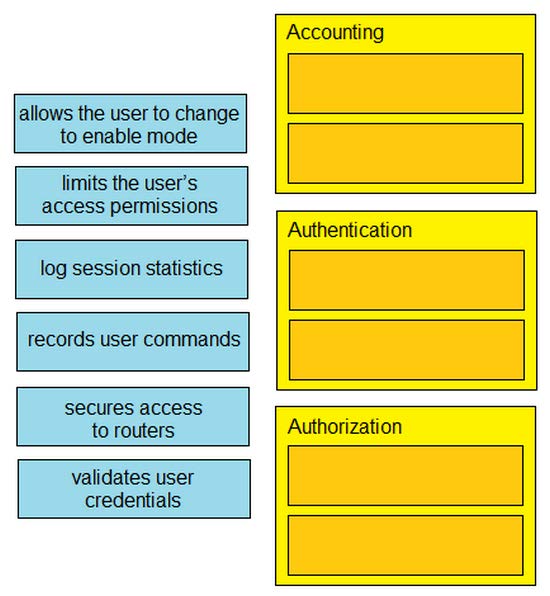
Correct Answer:

3,What are two benefits of private IPv4 addressing?
(Choose two.)
A. propagates routing information to WAN links
B. provides unlimited address ranges
C. reuses addresses at multiple sites
D. conserves globally unique address space
E. provides external internet network connectivity
Correct Answer: CD
4.Which technique can you use to route IPv6 traffic over an IPv4 infrastructure?
A. NAT
B. 6 to 4 tunneling
C. L2TPv3
D. dual-stack
Correct Answer: B
Overlay tunneling encapsulates IPv6 packets in IPv4 packets for delivery across an IPv4 infrastructure (a core network or the figure below).
By using overlay tunnels, you can communicate with isolated IPv6 networks without upgrading the IPv4 infrastructure between them.
Overlay tunnels can be configured between border devices or between a border device and a host; however, both tunnel endpoints must support both the IPv4 and IPv6 protocol stacks.
IPv6 supports the following types of overlay tunneling mechanisms:
1 Manual 2 Generic routing encapsulation (GRE) 3 IPv4-compatible 4 6to4 5 Intrasite Automatic Tunnel Addressing Protocol (ISATAP)
5.Which two network actions occur within the data plane?
(Choose two.)
A. Run routing protocols.
B. Make a configuration change from an incoming NETCONF RPC.
C. Add or remove an 802.1Q trunking header.
D. Match the destination MAC address to the MAC address table.
E. Reply to an incoming ICMP echo request.
Correct Answer: CD
https://www.ciscopress.com/articles/article.asp?p=2995354andseqNum=2
De-encapsulating and re-encapsulating a packet in a data-link frame (routers, Layer 3 switches)
Adding or removing an 802.1Q trunking header (routers and switches)
Matching an Ethernet frame\’s destination Media Access Control (MAC) address to the MAC address table (Layer 2 switches)
Matching an IP packet\’s destination IP address to the IP routing table (routers, Layer 3 switches)
Encrypting the data and adding a new IP header (for virtual private network [VPN] processing)
Changing the source or destination IP address (for Network Address Translation [NAT] processing)
Discarding a message due to a filter (access control lists [ACLs], port security)
All the items in the list make up the data plane, because the data plane includes all actions done per message.
6.What is the purpose of the service-set identifier?
A. It identifies the wireless network to which an application must connect.
B. It identifies the wired network to which a network device is connected.
C. It identifies the wired network to which a user device is connected.
D. It identifies a wireless network for a mobile device to connect.
Correct Answer: D
The admins need to sort this out, would be useless without the knowlegable folk in the discussion section.
7.Where does a switch maintain DHCP snooping information?
A. in the MAC address table
B. in the CAM table
C. in the binding database
D. in the frame forwarding database
Correct Answer: C
The DHCP snooping binding database is also referred to as the DHCP snooping binding table.The DHCP snooping feature dynamically builds and maintains the database using information extracted from intercepted DHCP messages.
The database contains an entry for each untrusted host with a leased IP address if the host is associated with a VLAN that has DHCP snooping enabled.
The database does not contain entries for hosts connected through trusted interface
8.Which task on the neighbor device enables the new port channel to come up without negotiating the channel?
Refer to the exhibit.
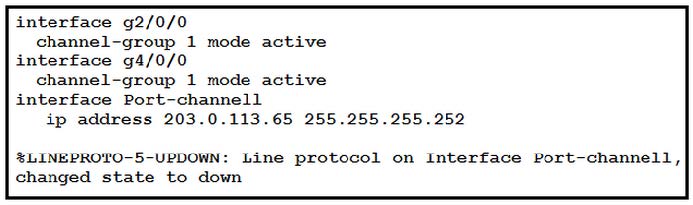
An engineer is configuring a Layer 3 port-channel interface with LACP. The configuration on the first device is complete, and it is verified that both interfaces have registered the neighbor device in the CDP table.
A. Change the EtherChannel mode on the neighboring interfaces to auto.
B. Configure the IP address of the neighboring device.
C. Bring up the neighboring interfaces using the no shutdown command.
D. Modify the static EtherChannel configuration of the device to passive mode.
Correct Answer: D
9.What is an Ansible inventory?
A. unit of Python code to be executed within Ansible
B. file that defines the target devices upon which commands and tasks are executed
C. device with Ansible installed that manages target devices
D. collection of actions to perform on target devices, expressed in YAML format
Correct Answer: B
10.DRAG DROP
Drag and drop the wireless standards from the left onto the number of nonoverlapping channels they support on the right.
Select and Place:

Correct Answer:
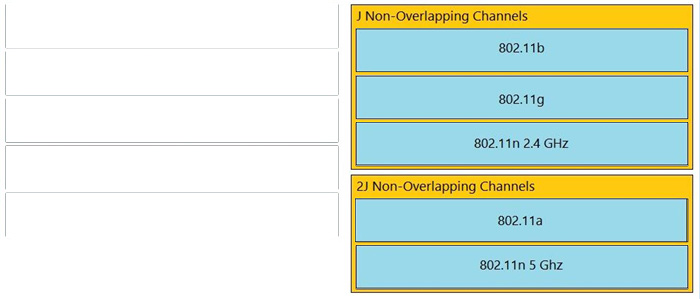
11.Which protocol is used for secure remote CLI access?
A. HTTPS
B. HTTP
C. Telnet
D. SSH
Correct Answer: D
12.What is the function of northbound API?
A. It upgrades software and restores files.
B. It relies on global provisioning and configuration.
C. It supports distributed processing for configuration.
D. It provides a path between an SDN controller and network applications.
Correct Answer: D
13.Which action completes this configuration?
Refer to the exhibit.
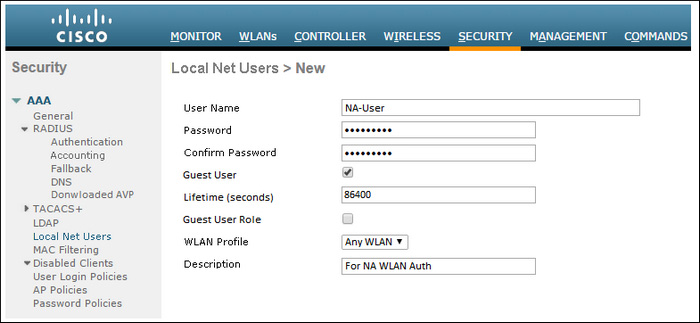
Wireless LAN access must be set up to force all clients from the NA WLAN to authenticate against the local database. The WLAN is configured for local EAP authentication. The time that users access the network must not be limited.
A. Uncheck the Guest User check box
B. Check the Guest User Role check box
C. Set the Lifetime (seconds) value to 0
D. Clear the Lifetime (seconds) value
Correct Answer: B
Lifetime valid range is 60 to 2,592,000 seconds, default is 86,400 seconds.
For unlimited time Guest User has to be unchecked,
14.What is the cause of the issue?
Refer to the exhibit.
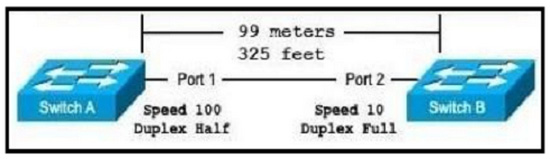
The switches are connected via a Cat5 Ethernet cable that is tested successfully. The interfaces are configured as access ports and are both in a down status.
A. The speed settings on the switches are mismatched
B. The distance between the two switches is not supported by Cat5
C. The switches are configured with incompatible duplex settings
D. The portfast command is missing from the configuration
Correct Answer: A
15.DRAG DROP
Drag and drop the IPv6 addresses from the left onto the corresponding address types on the right.
Select and Place:
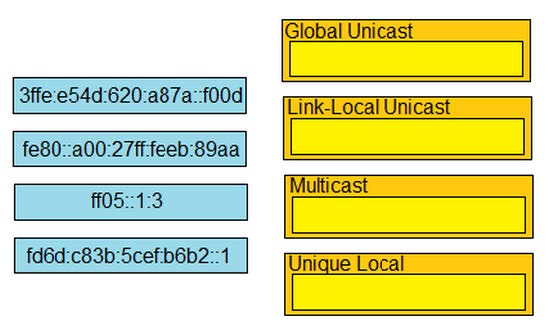
Correct Answer:

There’s more to come… Follow us for continuous free updates. You can also get the complete practice exam materials on the Pass4itsure CCNA 200-301 practice exam download page: https://www.pass4itsure.com/200-301.html.
We always ask ourselves one more question — what’s the next step?
After obtaining the CCNA 200-301 certification
The CCNA certification applies to a wide range of job scenarios, but it is still an entry-level certification. So if you’re looking to advance further, here are my recommendations.
| Advanced certification | Advanced direction | Free practice exam materials | Official information | |
| Network Engineer | CCNP Enterprise,Cisco DevNet Professional | Enterprise network design, configuration, and maintenance, involving routing, switching, wireless, and SD-WAN. | https://www.exammodule.com/category/ccnp-enterprise/ | https://www.cisco.com/site/us/en/learn/training-certifications/certifications/enterprise/ccnp-enterprise/index.html |
| Cybersecurity Engineer | CCNP Security,Cisco CyberOps Associate,CompTIA Security+ | Network security, configure firewalls, IDS/IPS, and respond to network threats. | https://www.exampass.net/latest-cisco-dumps/cisco-ccnp-dumps | https://www.cisco.com/site/us/en/learn/training-certifications/certifications/security/ccnp-security/index.html |
| Network Automation Engineer | Cisco DevNet Associate/Professional,AWS Certified Solutions Architect | Use programming to automate network configuration and management, adapting to cloud and SDN environments. | https://www.exampass.net/latest-cisco-dumps/cisco-devnet-dumps | https://www.cisco.com/site/us/en/learn/training-certifications/certifications/devnet/associate/index.html |
| Cloud Network Engineer | AWS Certified Advanced Networking,Azure Network Engineer Associate | Use programming to automate network configuration and management, adapting to cloud and SDN environments. | https://awsexamdumps.com/ | https://aws.amazon.com/certification/certified-advanced-networking-specialty/ |
These pieces of information should help you avoid detours. Use Pass4itsure practice exams to easily achieve your goals. Finally, I wish you progress and a career breakthrough.